Security Solutions - Group IB: ASM Solution AssetZero
- SAP Business One
- Darktrace
- BeyondTrust
- Group IB
- Claroty
- NetMan
- ASM Solution AssetZero
- DRP(Digital Risk Protection)
"In business, a single unmanaged vulnerability can result in disastrous consequences."
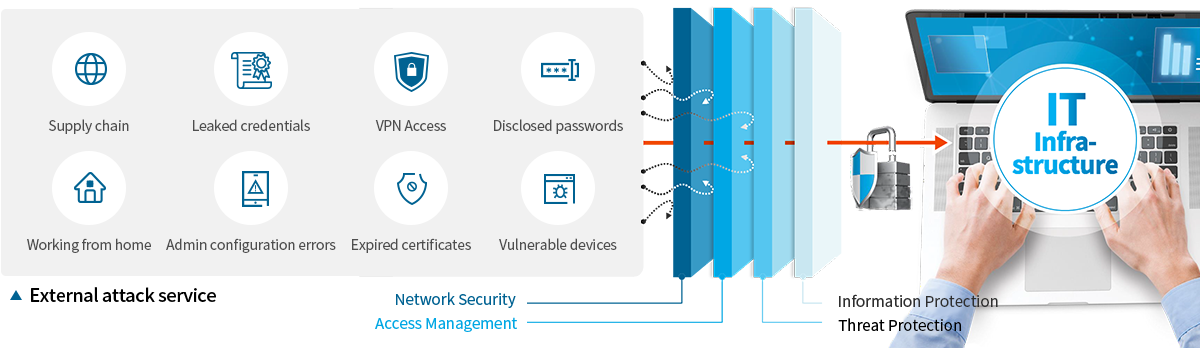
AssetZerois an intelligence-driven, integrated attack surface management solution offered as SaaS.
-
 Diverse sources based on intelligence
Diverse sources based on intelligence
Provides various views from the attacker’s point of view -
 Data offered as SaaS simple to set up and operate
Data offered as SaaS simple to set up and operate -
 User-friendly UIs easy to solve or mitigate problems
User-friendly UIs easy to solve or mitigate problems -
 Brings value to all industries regardless of company size
Brings value to all industries regardless of company size
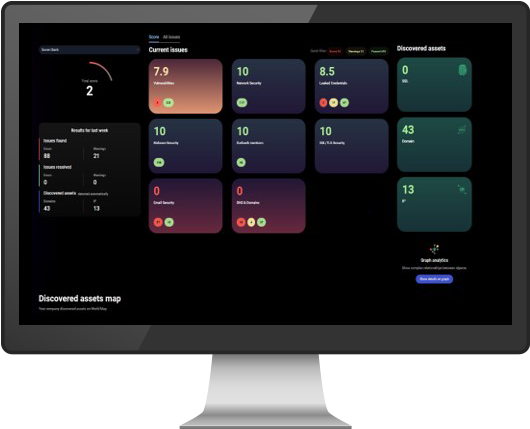
Provides general features necessary for ASM, such as asset identification, vulnerability scanning, and risk scoring.
- SCAN & Identify
- Constant scanning and identification
- IP Address
- Bucket storages
- SSL/TLS certificates
- SSL/TLS certificates
- Domain names
- Open software
- Validate & Categorize
- Asset validation and subsequent classification of assets
- Vulnerabilities
- Leaked Credentials
- Dark web mentions
- Email Security
- Network security
- Malware security
- SSL/TLS Security
- DNS & Domains
- Alert & Risk Score
- Alert generation and risk scoring
- Error : Urgent action required
- Warning : Further analysis required
- Passed : No issues detected
- Remediation & Engagement
- Recommendation of which action to take and integration with other tools
- All alerts sent via UIs and the sharing feature
- Provides recommendations according to risk type and action details
- Integration with SIEM, SOAR, etc. through APIs
- Track change & Reassess
- Tracks changes and reassesses the security status
- Eliminates resolved issues, evaluates new threats
- Ensuing recalculation of threat scores
- Reassesses the current security status of the company daily

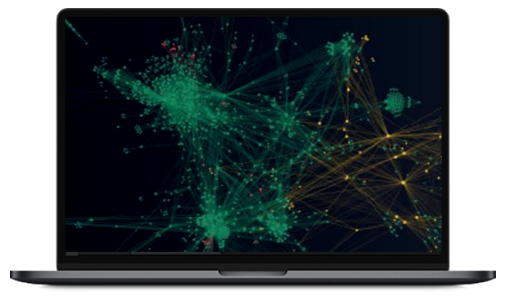
We offer exclusive value with our visual graph analysis tools and the best in industry intelligence.
-
01.Visualization of security status with advanced data visualization technology. Instant visualization of the overall attack surface as graphs.
Automatic connection between objects and maps related to searched sources. -
02.Provides context beyond the identified vulnerabilities. Offers data context based on the latest threat indicators.
Determines the severity of the threat based on attacks found in the real world. -
03.Uses the top industry intelligence. Intelligence directly related to hackings, including C2 servers and phishing collection points.
Tracks leak information and hacker activities from dark web. -
04.Detects malicious activities of attackers. Detects phishing, defacement attacks, malicious communication and infrastructure.
Exclusive feature that identifies malicious code embedded on websites.
Offers 100% visibility that eliminates and mitigates attack surface risks by providing actionable advice.

-
- Gain visibility into attack surface assets.
- Obtain complete visibility into the company's
external attack surface, including unknown assets. - Manage the history of changed assets
through continuous scanning.
-
- Offers actionable advice.
-
Scores risks based on detected vulnerabilities,
and present priorities that must be tackled immediately. -
Proactive response before the attack by offering insights from the perspective of the attacker
and actual threats taking place in the wild.
-
- Create a resilient security posture
against the dark web. - Detect various account info leaked from the company
that can be used as a first point of entry in attacks. - Protect the company brand against phishing, etc.
- Identify and respond to signs of attacks on the company
currently being discussed in underground forums, etc.
- Create a resilient security posture
-
- Integration with and maximum use of
existing tools. -
Put comprehensive security control in place
including external attack surface by integrating with intrusion prevention solutions including SIEM and SOAR. - Maximize the use of existing solutions by integrating with other firewalls and IPS that support API Interface.
- Integration with and maximum use of