Security Solutions - DRP(Digital Risk Protection)
- SAP Business One
- Darktrace
- BeyondTrust
- Group IB
- Claroty
- NetMan
- ASM Solution AssetZero
- DRP(Digital Risk Protection)
 Why digital assets should be identified and managed?
Why digital assets should be identified and managed? 
You should protect your digital assets and brand in the evolving online business and digital ecosystem.
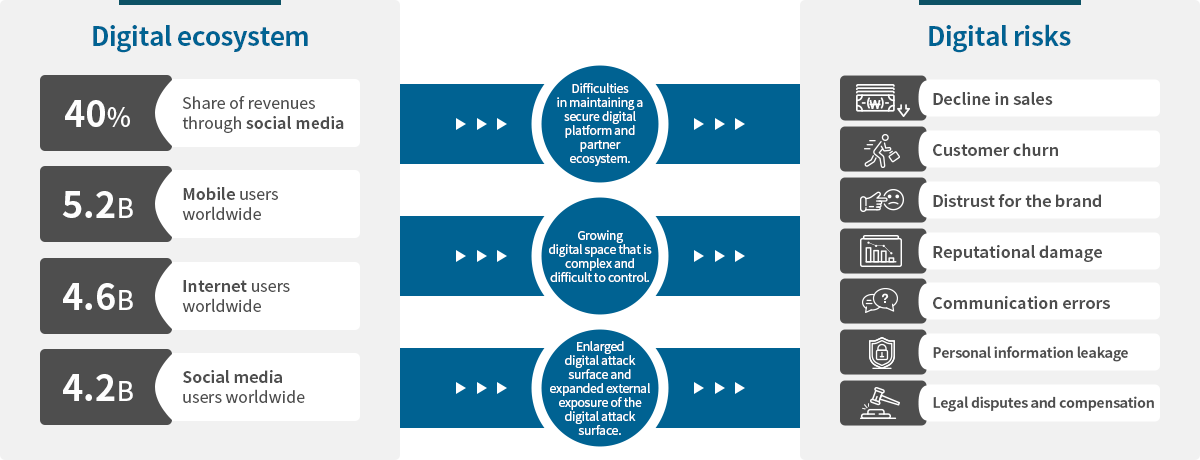
Digital ecosystem
- Difficulties in maintaining a secure digital platform and partner ecosystem.
- Growing digital space that is complex and difficult to control.
- Enlarged digital attack surface and expanded external exposure of the digital attack surface.
Digital risks
-
 Decline in sales
Decline in sales
-
 Customer churn
Customer churn
-
 Distrust for the brand
Distrust for the brand
-
 Reputational damage
Reputational damage
-
 Communication errors
Communication errors
-
 Personal information leakage
Personal information leakage
-
 Legal disputes and compensation
Legal disputes and compensation
DRP modules and features provided by each module
-
01 BrandANTI-SCAM
abuse- Defend against online brand abuse.
- Prevent scams and phishing.
- Detect fake partnerships and prevent trademark abuse.
- Discover fake advertisements.
- Detect fake accounts and groups on social media.
- Identify fake mobile apps.
-
02 CounterfeitANTI-COUNTERFIET
goods- Prevent the sales of illegal goods and services.
- Detect the selling of illegal goods on the Internet.
- Identify grey import in the illegal import market.
- Detect partner agreement violations.
-
03 CopyrightANTI-PIRACY
infringement- Block illegal digital content distribution.
- Video content.
- Online streaming content.
- Software and game content.
- Books, newspapers, articles.
- Music files.
-
04 InformationLEAK DETECTION
leakage- Sensitive information leakage on the dark web.
- Account information (credential) leakage.
- Source code leakage.
- Corporate confidential data leakage.
-
05 VIPVIP PROTECTION
impersonation- Detect and remove fake online accounts impersonating VIPs.
- Identify fake accounts on social media.
- Monitor all information about VIPs online.
Mechanism and technology of DRP solution
3 steps from resource monitoring to the detection and elimination of violations.

-
STEP 01 Monitor

 Monitor Digital Assets
Monitor Digital Assets- Domain name
- DB Phishing resource DB
- Search engine
- Code repository
- Social media
- Mobile app store
- Online market
- Instance message
- Online advertisement
- Deep/dark web
-
STEP 02 Detect

 Detect Infringements
Detect Infringements- Phishing and scam
- Counterfeit goods
- Brand abuse
- Counterfeit/falsified app
- Trademark abuse
- Partnership violation
- Fake advertisements
- Illegal reproduction
- VIP impersonation
- Sensitive information leakage
-
STEP 03 Response
 Eliminates violations
Eliminates violations- 3-step takedown service

- ① Notification
- ② Escalation
- ③ C&D
- 3-step takedown service

-
- Comprehensively manage external online digital assets.
- Provide full visibility into all online digital assets of your company (e.g., domain, brand, product, trademark, VIP).
- Support the establishment of R&R and work processes related to corporate digital asset management using automated solutions.
-
- Respond proactively to sales and corporate reputation risks.
- Prevent direct sales loss and expected customer churn that may occur due to phishing, counterfeit brand (product).
- Act preemptively with relation to corporate reputational damage due to exposure of sensitive information on the dark web, VIP impersonation, and damage caused by phishing/fake websites.
-
- Protect corporate image in case of illegal activity.
- Immediately take down detected illegal acts to minimize customer damage.
- Inform subscribers of relevant information, promote the company's differentiated readiness and response system for online illegal acts, and protect the brand.
-
- Secure digital evidence in preparation for legal disputes and audits.
- In the case of an audit by a higher authority in relation to illegal acts, present digital evidence proving the company's active response.
- In case of legal disputes, prepare detailed digital evidence to prove illegality of counterpart.
